CONFIDENCE BY DESIGN
GAME CHANGER_
Test with the smartest JavaScript injections ever.FUTURE IS HERE_
Join the next revolution in offensive security tools.FEATURING
TYPES
Source-based XSS
- HTML Context
- JavaScript Context
- XML Context
.
DOM-based XSS
- Document Sink
- Location Sink
- Execution Sink
Blind XSS (email report)
- Custom Payloads
- Automatic Injection
INJECTION
Input Scope
- POST Body parameters (value and name)
- URL Parameters (value and name)
- URL Path (3 levels deep)
- URL Fragment
Input Techniques
- Base64 and Double Encode
- Multi injection and Multi Context
- Parameter Guessing
Input Authentication
- User provided headers
EXCLUSIVE
Modes
- XSS Polyglots
- PoC Checking
ReferenceError Fix
- JS Object Hoisting
- JS Hoisting Override
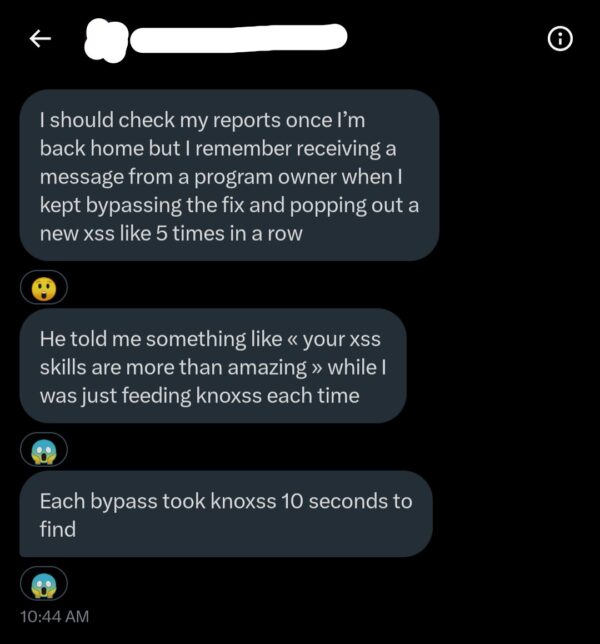
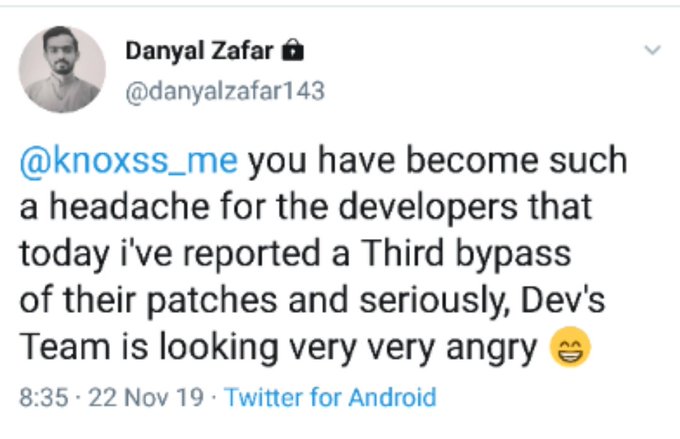
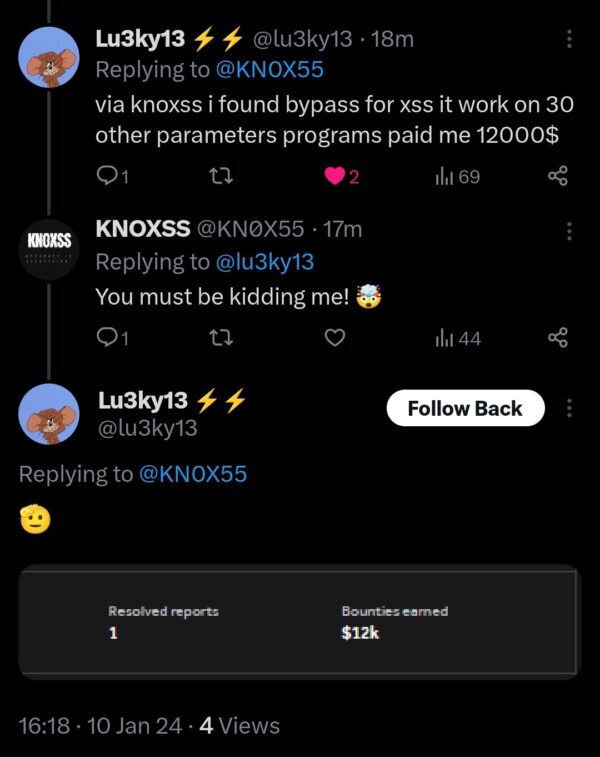
Filter Bypass
- Fully validated URL and email formats
- Hardcoded Obfuscation
- Evasion using I/O differences
- Basic CSP bypass
Frequently Asked Questions
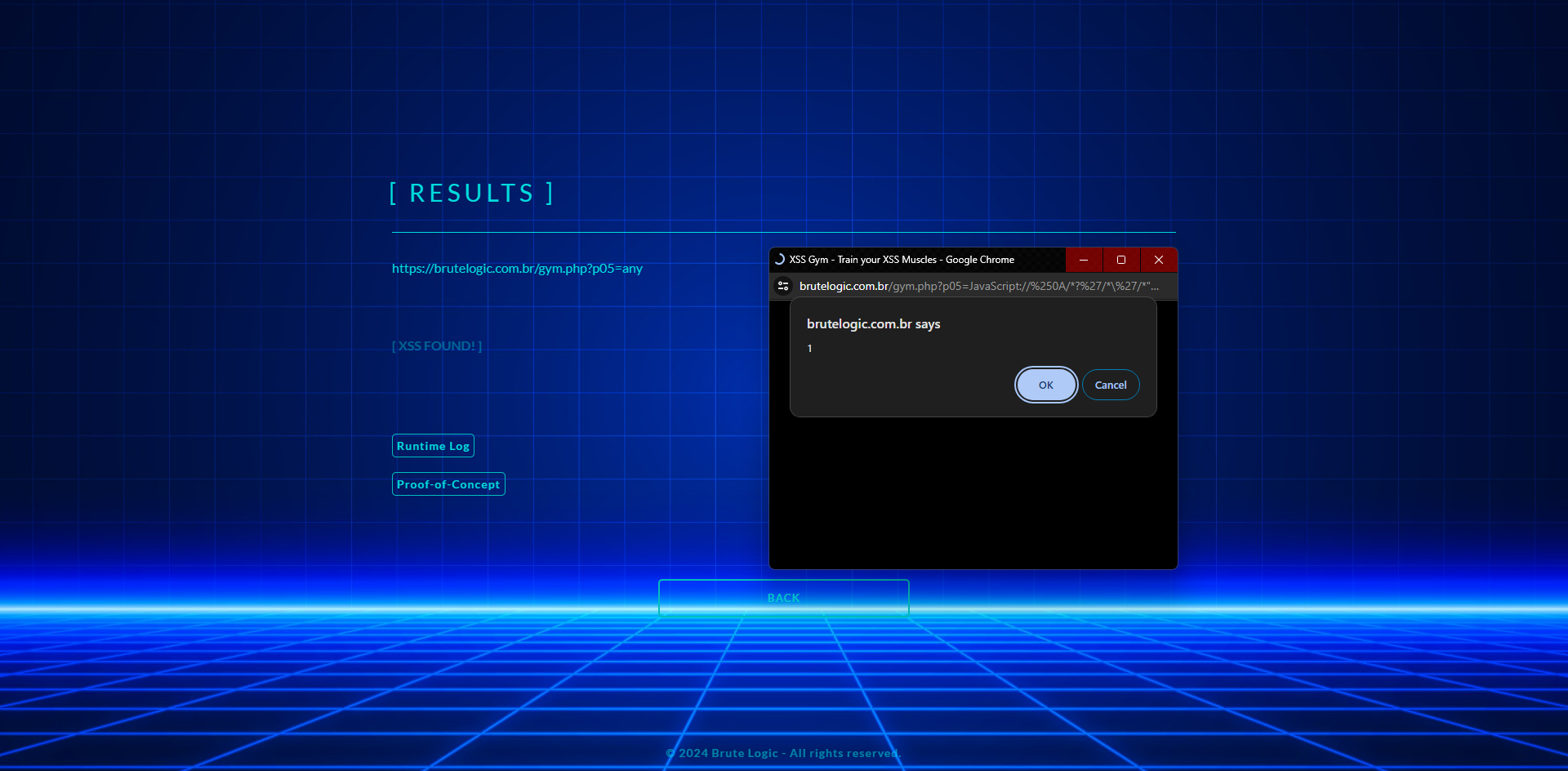
What KNOXSS does?
KNOXSS finds source-based and DOM-based reflected and stored XSS in vulnerable pages using components of URL (path and query parameters) as entry points. To see all XSS cases KNOXSS is able to spot check our XSS Coverage.
How to use KNOXSS?
The basic usage is just copy + paste the target URL in the main field of the web user interface (at knoxss.pro/ui). That's for unauthenticated GET requests, most scenarios out there. For POST requests, there's the need to provide the action URL in the main field and the POST body (pairs of name=value separated by a & sign) in the left box after clicking in the "Extra Data" button. For authenticated requests, there's a right box after clicking in "Extra Data" to provide pairs of HTTP headers (usually cookies) in the format header:value, one per line.
How KNOXSS works?
Basically, KNOXSS takes the target URL plus all extra data provided and check if there's a reflection on all URL or POST body parameter values (also on name), along with URL path (3 levels deep) and fragment. If it finds some reflection somewhere, in the HTTP response, DOM or associated JS calls, it will take some decisions on what type of injection it will use (HTML or JS injection). Finally it will try several specific XSS vectors in order to pop an alert box to prove the vulnerability.